)
On the Initial Access Broker markets of the underground, cybercriminals buy and sell access to compromised endpoints that equip them with the first step into their targets’ networks. Detecting and proactively containing access compromise is critical to reduce the risk of attack. With Cybersixgill’s Darkfeed, users can preemptively block the indicators of compromise used by access brokers before they have the chance to compromise their machine - stopping potential attacks in their heels before their network pops up for sale on the illicit marketplaces of the deep and dark web.
In the underground economy, the services of Initial Access Brokers are in high demand. Across Initial Access and Wholesale Access marketplaces, brokers sell access to compromised endpoints and organizational networks, allowing other cybercriminals to purchase their first entry point into their targets’ networks and, from there, carry out a larger attack within the organization. In the past year, Cybersixgill collected nearly 6.5 million compromised endpoints listed for sale on just one market.
These initial access vectors listed for sale have been directly linked to several recent cybersecurity breaches, demonstrating a clear correlation between access compromise on broker markets and subsequent victimization in high-profile attacks. For example, in the Uber breach, an attacker compromised an Uber EXT contractor's account, gaining unauthorized access to their network. Indeed, prior Cybersixgill research found that dozens of major ransomware attacks appear to have originated with access purchased in these markets for only $10 within 180 days prior to the attack.
With these markets posing such a major threat, how should companies protect themselves?
Protecting Against Access Compromise with Cybersixgill
Cybersixgill’s Investigative Portal and alerting mechanisms warn customers in real-time when access associated with their network is offered for sale on the underground, offering additional intelligence services to purchase the item and remove it from the market. In an ideal scenario, however, access to their network would not have been compromised in the first place.
Preemptive Infection Prevention with Darkfeed
The cybercriminal underground is replete with malicious threat actors offering various free and paid tools, programs and services to carry out an attack. One of the most popular ‘bestsellers’ is infostealer malware, which resides in an infected computer, quietly gathering data - including login credentials, cookies and keystrokes - that could allow threat actors to gain an initial access foothold into an organization’s network. Threat actors employ social engineering tactics such as phishing attacks, malvertising and malicious links to trick victims into infecting their machine with the malware, and exposing their sensitive data.
Cybersixgill’s Darkfeed, a comprehensive feed of Indicators of Compromise (IoCs), empowers organizations to preemptively block indicators before an attack occurs, providing an opportunity to protect employees from accidentally installing malicious programs like Raccoon Stealer. The Darkfeed seamlessly integrates with a wide variety of security solutions (and is also available in STIX/TAXII so that customers can use it to prevent endpoint compromise).
Now, let's explore how Darkfeed can play a crucial role in preemptively blocking malware infection in the first place. Figure 1 (below) depicts a listing posted on an Initial Access Broker market, offering various compromised endpoints for sale. In the listing, the broker notes that the stealer employed to compromise the machines was the Racoon stealer (sometimes referred to as Raccoon), as highlighted in red in the image. Figure 1. Listing in IAB market including reference of the Racoon stealer.
Figure 1. Listing in IAB market including reference of the Racoon stealer.
Using Anomali’s ThreatStream, or any other security tool with Darkfeed integration, we can sort through all of the observables, or indicators, that Cybersixgill has published (Figure 2). Figure 2. Sample of Cybersixgill-collected Raccoon indicators in Anomali ThreatStream.
Figure 2. Sample of Cybersixgill-collected Raccoon indicators in Anomali ThreatStream.
Darkfeed also provides rich contextual information for each indicator collected, such as source, threat actor, and confidence score, to help you prioritize and block these threats.
Post-infection Protection with the Investigative Portal
In large enterprises with a multitude of endpoint devices and remote employee network logins (perhaps sometimes from personal devices), just one weak link or a single human error could put the entire environment at risk. One compromised endpoint, if left exposed, could be a beachhead for total network compromise. It is therefore crucial to implement robust security measures to prevent compromised endpoint access from spiraling into a larger breach impacting the entire network.
As noted above, Cybersixgill’s Investigative Portal alerts users in real-time of potential initial access compromise. These instantaneous alerts provide the critical early warning needed to identify, prevent, and remediate unauthorized access in time, before the access is weaponized in attack. Figure 3, below, depicts a listing on an Initial Access Broker market advertising an endpoint with access to ADFS:
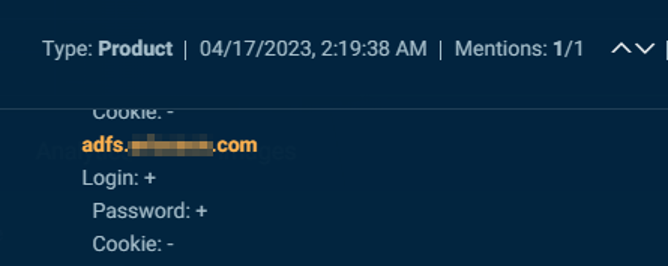 Figure 3. An account with access to ADFS compromised and placed for sale on 4/17/23.
Figure 3. An account with access to ADFS compromised and placed for sale on 4/17/23.
Remediation
If this endpoint for sale was attributed to one of our customers, they would receive an alert in real-time to the exposure. They could then effectively remediate the situation by leveraging our Intelligence Services offering for Dark Web Purchases. Through this service, we actively purchase the compromised account directly from the market, extract the victim's details, and provide them back to the user for further remediation and forensic investigation. Typical remedial actions include resetting permissions and passwords, as well as performing a thorough wipe of the identified compromised machine to ensure complete removal of the threat.
Conclusion
Darkfeed, our comprehensive and continuously updated feed of indicators of compromise, is a powerful tool in proactive infection prevention. By integrating Darkfeed into your security infrastructure, you can identify and block indicators associated with known access compromise threats such as the Racoon stealer. This proactive approach significantly reduces the likelihood of successful attacks and enhances your overall security posture.
At Cybersixgill, we are dedicated to empowering organizations with the necessary tools and intelligence to detect, prevent, and mitigate cyber threats. By leveraging Darkfeed alongside our extensive suite of services, you can strengthen your defenses, ensure timely remediation, and safeguard your critical assets from malicious actors.
Join Michael-Angelo Zummo in our webinar, "Darkfeed: Combatting Initial Access," to delve deeper into Cybersixgill's Darkfeed and expand your knowledge. Register now.
)
)
)
)