)
If you work in cybersecurity, your work is impacted every day by what happens on the deep and dark web – whether you can see it or not.
Not only do threat actors turn to the deep and dark web when they want to communicate anonymously, but they do so in a way that drives an underground economy in which tools for executing cybercrimes (some of which are themselves derived from previous cybercrimes) are bought and sold.
The result is an ecosystem in which a variety of threat actors effectively work together to commit cyber attacks more sophisticated than what any one of them could carry out on their own.
All of that makes the deep and dark web – specifically, the portion of these underground sources that we at Cybersixgill often call the cybercrime underground – a vital source of threat intelligence.
That also makes it especially important for cybersecurity professionals to understand the big picture of what the cybercrime underground is, what happens there, and how it affects cybersecurity globally.
That’s why we recently teamed up with Radware to offer an informative session on the deep and dark web at SOCstock 2021.
Together with Daniel Smith, the head of cyber threat intelligence research at Radware, I took the opportunity to give an overview of the cybercrime underground and share some of the most important insights I’ve learned over the years I’ve spent investigating what goes on there.
Not only did Daniel and I offer a crash course on what happens on the deep and dark web in general, but we also explored how the COVID-19 outbreak has impacted that underground activity – both criminal and otherwise.
Keep reading for the most important lessons from our joint session, Beyond the Shadow of the Underground.
First things first: What’s the deep web, what’s the dark web, and what’s the difference?
The term deep web refers broadly to any internet content that is not indexed by search engines.
This is essentially anything that requires authentication, including university libraries and corporate networks – but it can also include personal emails and WhatsApp messages.
Just as you use messaging platforms to communicate securely, threat actors also use deep web platforms (such as Telegram) to collaborate and transact.
Consequently, elements of the deep web are very relevant for threat analysts.
In contrast, the term dark web refers to sites that are only accessible through a special browser (Tor), which hides a user’s identity and location.
The dark web’s focus on privacy makes it a popular channel for hackers, cybercriminals, and other threat actors who prioritize anonymity – although not every communication or transaction that takes place there is illegal.
The reality of the dark web is more complex, but we can think of it as functioning in two basic roles:
A collection of online communities.
A space for anonymous commerce and interaction.
Who is active on the dark web, and why?
The deep and dark web can be used by anyone who wants to communicate and transact anonymously.
This realm is not exclusive to the “bad guys.” There are actually many white-hat hackers who discuss cybersecurity – including by asking questions about problems their employers face, without providing threat actors with details that could put their employers at risk.
Enthusiasts flock to forums to chat about gaming, cryptocurrency, and tech products. Dissidents use the cloak of anonymity to remain protected against government surveillance.
And finally, we must be aware that journalists, law enforcement, intelligence agencies, and security professionals are present as well, trying to understand and even influence what’s going on.
However, among deep and dark web users, there are considerable numbers of threat actors involved in illegal enterprises – such as financial fraudsters, black-hat hackers, narcotics dealers, and traffickers of illegal goods and services.
The plurality of the dark web’s threat actors can be categorized as script kiddies – novices who carry out low-complexity, low-reward attacks, usually by using tools acquired from someone else.
Then, in smaller numbers, there are proficient hackers, who can employ more advanced tactics, techniques, and procedures.
Next, there are crime syndicates, which can carry out very sophisticated attacks due to advanced capabilities in hacking, fraud, and money laundering.
Finally, there are even smaller numbers of government actors – but, while we can be certain that they are present on the dark web, they never identify themselves.

>The levels of complexity of various types of threat actors and the scope of the rewards they typically enjoy
Notably, the types of attacks that we see emanating from the deep and dark web roughly follow a similar pattern.
The majority of attack mechanisms are low-complexity and low-reward, such as account checkers and password crackers. More advanced actors may be involved with cryptominers, ransomware, and the use of known exploits.
Meanwhile, only the most advanced actors possess and use zero-day exploits.
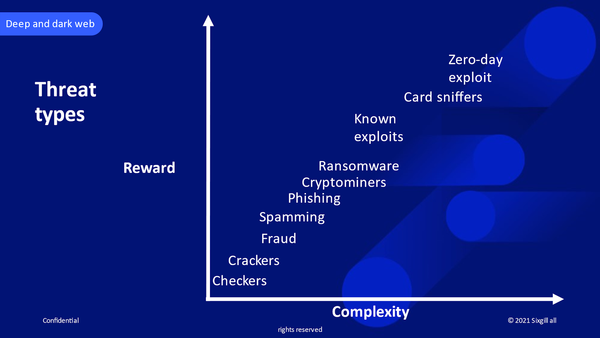
The levels of complexity of various types of cyberattacks and the scope of the rewards their perpetrators often enjoy
What types of intelligence can we find on the dark web?
Because actors use the deep and dark web for anonymous communication and commerce, we can use these sources to find intelligence in the spirit of those principles. This includes:
Chatter about news and developments.Many actors discuss relevant news in conversations comparable to what takes place on conventional social media sites. These conversations can cover global news (such as COVID-19 or politics) or more niche topics (such as gaming, technology, and cryptocurrency). Many also discuss developments in cybercrime. Following these conversations helps illuminate who is active on the deep and dark web.
Chatter about defensive measures and offensive TTPs.On the deep and dark web, many actors discuss the latest security threats and how to remain protected. Others discuss how to carry out attacks, whether simple or complex. By reviewing this chatter, analysts can come to understand preferred TTPs employed by specific actors.
Software-as-a-service.Threat actors offer software such as malware or ransomware, or other tools needed in order to carry out a cyberattack. Analysts can use this information to understand the availability of attack components, perhaps even assessing the likelihood that one will be used in an actual attack.
Attacks-as-a-service.Threat actors offer bespoke attacks (for example, “I’ll hack your ex-girlfriend’s Instagram”) or components necessary for carrying out larger attacks, such as network access, compromised infrastructure, and money laundering.
Sale of products.Threat actors sell products harvested from cyberattacks such as phishing or ransomware. Sold products can include compromised credit card numbers, credentials, and even access to hacked systems. The quantities and trends of sold products can indicate the scope of successful attacks.
Underground identities.Actors on the dark web remain anonymous. However, while we do not know who they are in real life, we can piece together their “underground identity,” with data points such as language, contact information, cryptocurrency wallets, and aliases. This allows analysts to build profiles of key actors.
Much of the criminal activity that takes place on the deep and dark web is related to the use of botnets – an aspect of the cybercrime underground into which Radware has unique insight.
As Daniel pointed out during our presentation, sometimes threat actors merely use the deep and dark web to discuss issues related to the development and deployment of botnets.
In other cases, they sell access to the (robotic) tools of the trade via the cybercrime underground – profiting off of a crimeware-as-a-service model in which exploits and malware can be purchased by hackers who will then use them to execute cyberattacks involving botnets.
In still other cases, hackers use the dark web to sell services such as DDoS-as-a-service offerings, in which customers hire hackers who then use botnets to disrupt online traffic.
And What Don't We Typically Find On The Dark Web?
As an overall principle, we do not expect to discover intelligence that would compromise an actor’s anonymity or commercial dealings. Therefore, we do not see real-world identities, nor can we identify if any actor actually belongs to an advanced persistent threat (APT).
Similarly, we do not often see threat actors exposing their detailed plans, nor freely distributing high-quality tools (such as military-grade zero-day exploits or TTPs).
Finally, we do not see high-quality products won from previous attacks (such as verified credit card numbers or banking credentials) being offered at no charge. Whoever wants items like these will have to pay.
How has COVID-19 impacted the cybercrime underground?
Although we typically see that the numbers of unique active users in underground forums increase exponentially over time, those growth rates suddenly jumped significantly in the early days of the COVID-19 outbreak in the U.S.
By examining the numbers of unique active users in five leading underground forums between 2015 and late 2020, we at Cybersixgill have found that growth rates ranged from 1% to 9.2% per month. Each of these five forums saw its growth rate climb sharply in the spring of 2020 and then drop a few months later.
Notably, the numbers of unique active users over this period show that one forum’s growth did not come at the expense of another forum. Instead, participation throughout the dark web has increased over time, especially during the early part of the coronavirus outbreak.
There are a number of factors that likely contributed to these trends, such as a rapid increase in people working from home, increased difficulty in finding work and earning money through legitimate means, a plethora of scams taking advantage of widespread fears, and interest in trying to steal stimulus payments.
Whatever threat actors’ exact motivations may be, after COVID-19 hit the U.S., both Radware and we at Cybersixgill saw an explosion of indications that people were interested in committing a wide variety of types of cybercrime.
And while it’s no surprise that cybercriminals have taken advantage of opportunities to make money as a result of the outbreak, Daniel noted that video games have also been a common target of cyberattacks – and not only due to financial motivations.
While money is one major incentive for cybercriminals to target video games, some are also driven by pride, revenge, general animosity, and simply a desire for random mischief.
Keeping up with the latest threat intelligence
The volume of information on the deep and dark web is massive and growing rapidly. And while not all of it relates directly to cybercrime, there is enough information that does reflect criminal intent to keep any cybersecurity professional busy around the clock.
Although we cannot expect individuals to keep track of all the threats evident on the deep and dark web on their own (after all, that’s what automation is for), understanding the overall role of the dark web is essential for anyone looking to make sense of the world of cybercrime.
Like the session I hosted together with Daniel Smith, this blog post has provided an introduction to the cybercrime underground. But to really benefit from the information transmitted via the deep and dark web, robust cybersecurity teams need to pay attention to these channels on an ongoing basis – whether through automated alerts, by conducting investigations, or (ideally) both.
Simply put, the cybercrime underground puts all of us at risk by helping threat actors to work together – but it’s also a gold mine of cyber threat intelligence. It’s up to cybersecurity professionals to continually tap into that gold mine.
)
)
)
)